squerol
Advanced Cheater
![]() Reputation: 2 Reputation: 2
Joined: 06 Jul 2015
Posts: 65
Location: Poland
|
 Posted: Sat Dec 14, 2019 4:22 am Post subject: AOB to get base adress for pointer - what am I doing wrong? Posted: Sat Dec 14, 2019 4:22 am Post subject: AOB to get base adress for pointer - what am I doing wrong? |
 |
|
Hello.
I've got tired of time consuming unreliable pointerscan method to find pointers so I wanted to try something new.
I've found this guide about AOB injections to find base adress to wanted pointers ("Injection Copies" section of guide)...
https://web.archive.org/web/20171019202636/http://forum.cheatengine.org/viewtopic.php?t=572465
...but sadly after studying it and trying by myself my script won't execute (no errors, just can't check the box)
So, what I did (game is Nioh 1.21.05):
1. Found wanted adress,

2. Clicked "found what accesses this adress" on it,
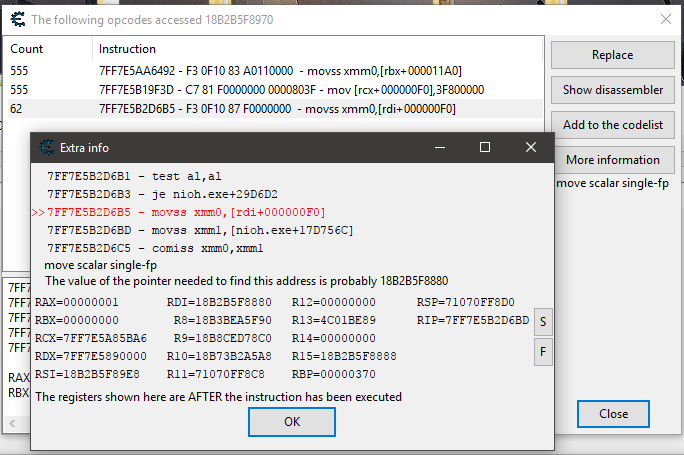
3. Got 3 results. By following guide, I've tested every one of it - so "show disassembler", and then "find out what adresses this instruction accesses" on highlited instruction in disassembler window.
The instructions from first 2 opcodes pointed to multiple adresses. Luckily, the instruction from third opcode pointed only to one adress which is the wanted one.
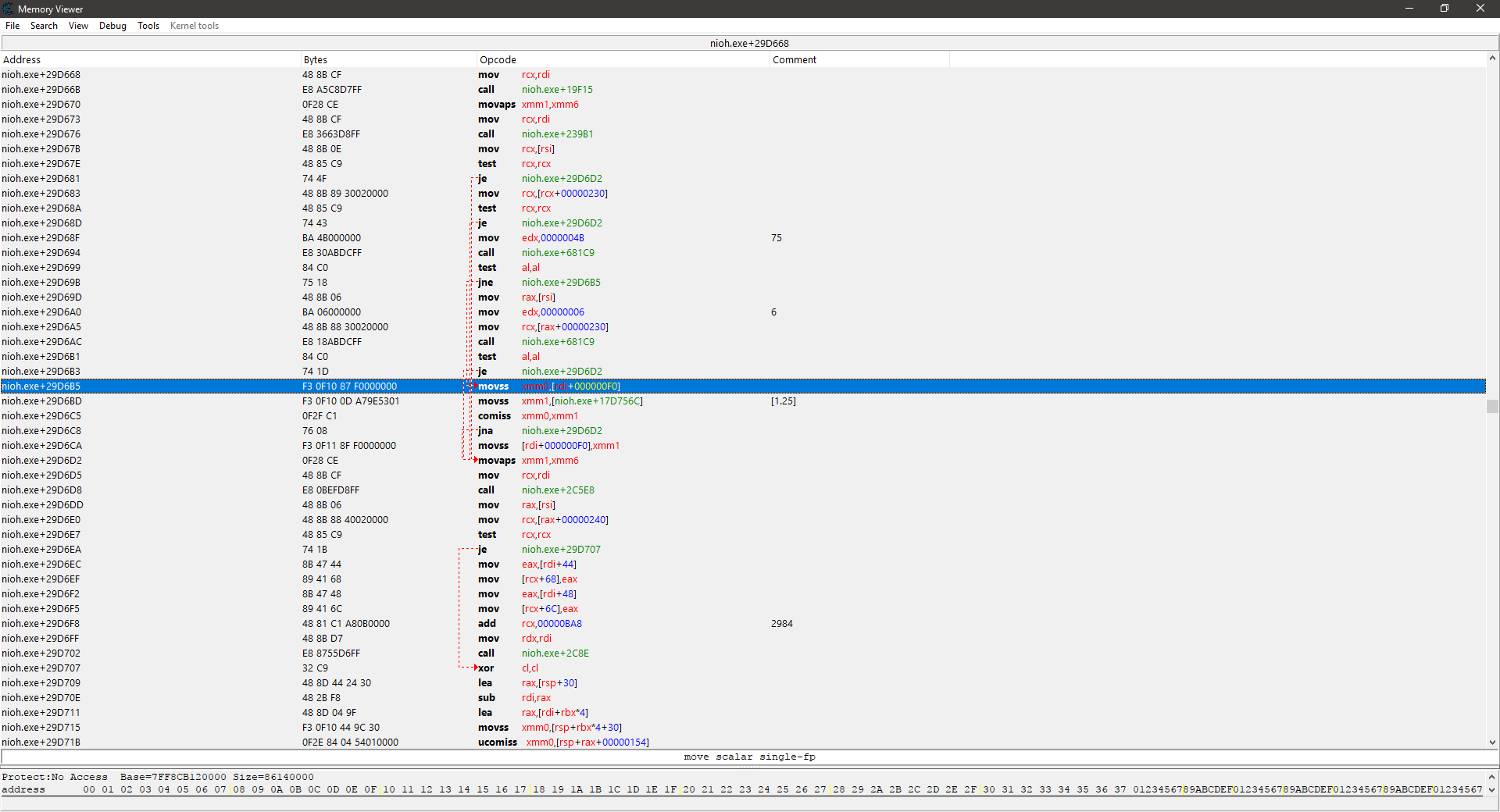
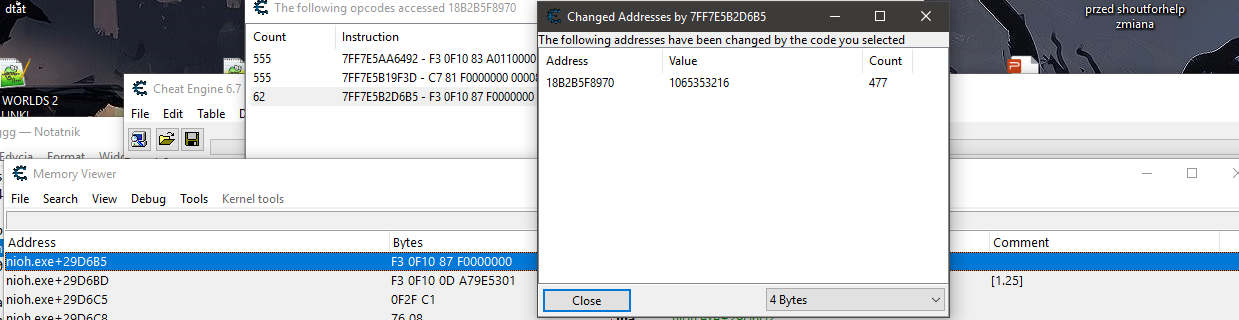
4. Done AOB injection script by following guide already mentioned before :
What I did (added just two lines globalalloc(_playerbase,4) and mov [_playerbase],rdi):
| Code: |
[ENABLE]
aobscanmodule(blabla,nioh.exe,F3 0F 10 87 F0 00 00 00 F3 0F 10 0D)
alloc(newmem,$1000,"nioh.exe"+29D6B5)
label(code)
label(return)
globalalloc(_playerbase,4)
newmem:
code:
mov [_playerbase],rdi
movss xmm0,[rdi+000000F0]
jmp return
blabla:
jmp newmem
nop
nop
nop
return:
registersymbol(blabla)
[DISABLE]
blabla:
db F3 0F 10 87 F0 00 00 00
unregistersymbol(blabla)
dealloc(newmem)
{
// ORIGINAL CODE - INJECTION POINT: "nioh.exe"+29D6B5
"nioh.exe"+29D68F: BA 4B 00 00 00 - mov edx,0000004B
"nioh.exe"+29D694: E8 30 AB DC FF - call nioh.exe+681C9
"nioh.exe"+29D699: 84 C0 - test al,al
"nioh.exe"+29D69B: 75 18 - jne nioh.exe+29D6B5
"nioh.exe"+29D69D: 48 8B 06 - mov rax,[rsi]
"nioh.exe"+29D6A0: BA 06 00 00 00 - mov edx,00000006
"nioh.exe"+29D6A5: 48 8B 88 30 02 00 00 - mov rcx,[rax+00000230]
"nioh.exe"+29D6AC: E8 18 AB DC FF - call nioh.exe+681C9
"nioh.exe"+29D6B1: 84 C0 - test al,al
"nioh.exe"+29D6B3: 74 1D - je nioh.exe+29D6D2
// ---------- INJECTING HERE ----------
"nioh.exe"+29D6B5: F3 0F 10 87 F0 00 00 00 - movss xmm0,[rdi+000000F0]
// ---------- DONE INJECTING ----------
"nioh.exe"+29D6BD: F3 0F 10 0D A7 9E 53 01 - movss xmm1,[nioh.exe+17D756C]
"nioh.exe"+29D6C5: 0F 2F C1 - comiss xmm0,xmm1
"nioh.exe"+29D6C8: 76 08 - jna nioh.exe+29D6D2
"nioh.exe"+29D6CA: F3 0F 11 8F F0 00 00 00 - movss [rdi+000000F0],xmm1
"nioh.exe"+29D6D2: 0F 28 CE - movaps xmm1,xmm6
"nioh.exe"+29D6D5: 48 8B CF - mov rcx,rdi
"nioh.exe"+29D6D8: E8 0B EF D8 FF - call nioh.exe+2C5E8
"nioh.exe"+29D6DD: 48 8B 06 - mov rax,[rsi]
"nioh.exe"+29D6E0: 48 8B 88 40 02 00 00 - mov rcx,[rax+00000240]
"nioh.exe"+29D6E7: 48 85 C9 - test rcx,rcx
}
|
How script looked before editing, right after generating its template:
| Code: |
[ENABLE]
aobscanmodule(blabla,nioh.exe,F3 0F 10 87 F0 00 00 00 F3 0F 10 0D)
alloc(newmem,$1000,"nioh.exe"+29D6B5)
label(code)
label(return)
newmem:
code:
movss xmm0,[rdi+000000F0]
jmp return
blabla:
jmp newmem
nop
nop
nop
return:
registersymbol(blabla)
[DISABLE]
blabla:
db F3 0F 10 87 F0 00 00 00
unregistersymbol(blabla)
dealloc(newmem)
|
5. Saved it to my table, trying to execute it but nope. No error, no freeze, nothing. Checkbox of script won't check.
So... What am I doing wrong here?
Thank You for any suggestions.
PS. please don't beat me, except simple value search, pointerscanning and noping intructions my cheatengine expierience is next to none.
EDIT:::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::::
Ok, I've read somewhere else that:
| Code: | | globalalloc(_playerbase,4) |
...should be:
| Code: | | globalalloc(_playerbase,8) |
...for 64 bit game like nioh
Also I've replaced:
| Code: |
mov [_playerbase],rdi
|
with code found in this thread https://forum.cheatengine.org/viewtopic.php?t=611359:
| Code: |
push rax
mov rax,_playerbase
mov [rax],rdi
pop rax
|
...and now base adress after activating script works and I can set reliable pointer for it manually (_playerbase with f0 offset).
_________________
|
|








