| View previous topic :: View next topic |
| Author |
Message |
Mitch25
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Aug 2013
Posts: 7
|
 Posted: Sun Aug 25, 2013 7:22 pm Post subject: C# code only works after CE debugger is attached Posted: Sun Aug 25, 2013 7:22 pm Post subject: C# code only works after CE debugger is attached |
 |
|
My C# code works perfectly, but only after I use CE and do "Find out what accesses this address" (on the address of the value Im interested in) and the debugger is attached. My code even continues to then work after CE is closed.
Obviously I'd like this to work without having to go through this process..
I'm using the VEH debugger.
Any idea why this is happening? Any way to help me out here?
Code:
| Code: |
private Process[] processes;
private Process process = null;
private float lightColourScale = 0.0f;
private long lcsAddress;
private int lcsOffset = 0x550;
private IntPtr wow64cpu_BaseAddress;
private void FormMain_Load(object sender, EventArgs e)
{
processes = Process.GetProcessesByName("Napoleon");
if (processes.Length > 0)
{
process = processes[0];
}
else
{
return;
}
ProcessModuleCollection modules = process.Modules;
foreach (ProcessModule m in modules)
{
if (m.ModuleName == "wow64cpu.dll")
{
wow64cpu_BaseAddress = m.BaseAddress;
}
}
GetLightColourScaleAddress();
labelLightColourScale.Text = lightColourScale.ToString();
}
private void GetLightColourScaleAddress()
{
string addressString = (wow64cpu_BaseAddress + 0x00004720).ToString("X");
long baseAddress = long.Parse(addressString, NumberStyles.HexNumber);
int bytesRead;
byte[] buffer = new byte[4];
buffer = ReadMemory(baseAddress, 4, out bytesRead);
Array.Reverse(buffer);
addressString = BitConverter.ToString(buffer, 0, 4);
addressString = addressString.Replace("-", "");
int floatAddress = int.Parse(addressString, NumberStyles.HexNumber);
buffer = ReadMemory(floatAddress + lcsOffset, 4, out bytesRead);
lightColourScale = BitConverter.ToSingle(buffer, 0);
lcsAddress = floatAddress + lcsOffset;
}
public byte[] ReadMemory(long address, int numOfBytes, out int bytesRead)
{
IntPtr hProc = OpenProcess(ProcessAccessFlags.All, false, process.Id);
byte[] buffer = new byte[numOfBytes];
ReadProcessMemory(hProc, new IntPtr(address), buffer, numOfBytes, out bytesRead);
return buffer;
}
|
Thanks for your time!
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25832
Location: The netherlands
|
 Posted: Sun Aug 25, 2013 7:35 pm Post subject: Posted: Sun Aug 25, 2013 7:35 pm Post subject: |
 |
|
wow64cpu.dll is a bad module to use as it's a system module
As for why it works when the veh debugger is attached is because you're following a path generated by the veh debugger. (e.g the last state when a breakpoint was hit is stored in the target process)
use a different pointer (most likely more than 2 levels)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Mitch25
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Aug 2013
Posts: 7
|
 Posted: Mon Aug 26, 2013 11:28 am Post subject: Posted: Mon Aug 26, 2013 11:28 am Post subject: |
 |
|
Thanks for your reply,
I must admit I'm unsure as to where to go from here, being fairly new to Cheat Engine.
If the addresses given to me are unusable because of the fact the debugger is active then how do I find a different pointer?
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25832
Location: The netherlands
|
 Posted: Mon Aug 26, 2013 11:41 am Post subject: Posted: Mon Aug 26, 2013 11:41 am Post subject: |
 |
|
How did you find the pointer in the first place?
Just try a different path. E.g: instead of picking the first result pick a second one, or last one...
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Mitch25
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Aug 2013
Posts: 7
|
 Posted: Mon Aug 26, 2013 12:43 pm Post subject: Posted: Mon Aug 26, 2013 12:43 pm Post subject: |
 |
|
My method was this..
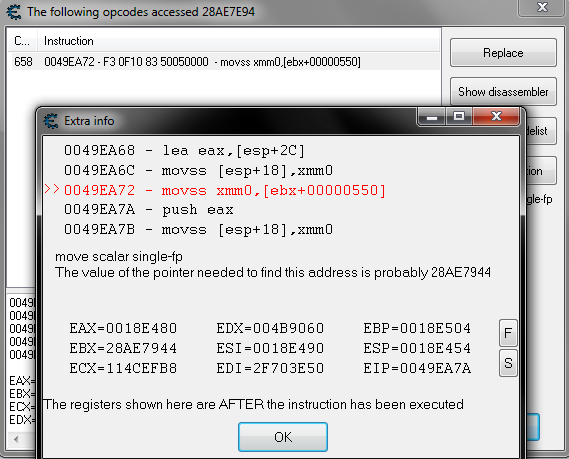
Scan for my value, find out what accesses the address of the value. The only one was this:
[See first image]
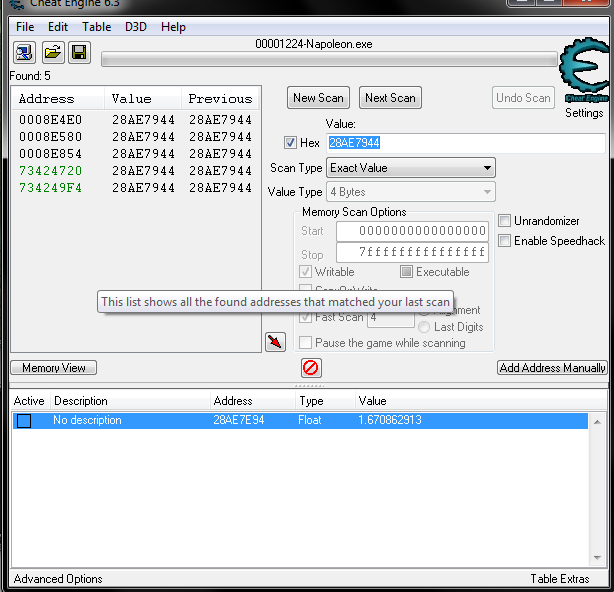
Scan for that address which revealed these:
[See second image]
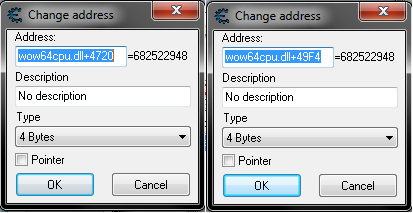
Both static addresses were always:
wow64cpu.dll+4720
wow64cpu.dll+49F4
[See last image]
Your post gave me the idea that it might be something to do with the fact that I was running CE x64, so I switched to x86.
Now when I do the above I get the same addresses as the last image, but the two bottom ones aren't static.
This I guess is where I'm getting lost..
I've tried adding the addresses manually and then doing "Find out what accesses this address" on them but the game then crashes.
| Description: |
|
| Filesize: |
40.34 KB |
| Viewed: |
9935 Time(s) |
|
| Description: |
|
| Filesize: |
42.86 KB |
| Viewed: |
9935 Time(s) |
|
| Description: |
|
| Filesize: |
16.33 KB |
| Viewed: |
9935 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25832
Location: The netherlands
|
 Posted: Mon Aug 26, 2013 1:09 pm Post subject: Posted: Mon Aug 26, 2013 1:09 pm Post subject: |
 |
|
Don't pick the static if they are system dll's. Find out what accesses the black ones(8e4e0) and go from there
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
Mitch25
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Aug 2013
Posts: 7
|
 Posted: Mon Aug 26, 2013 1:41 pm Post subject: Posted: Mon Aug 26, 2013 1:41 pm Post subject: |
 |
|
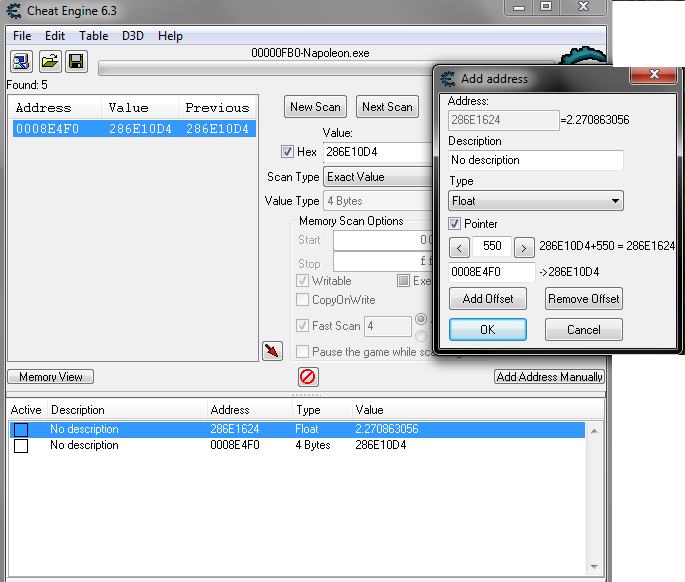
Right, I narrowed down my addresses to one as it was the only one not changing.
I added a new address as a pointer with that address and my initial offset of 550. And it does equal the value its meant to 2.270863. As can be seen in the attached image.
So now I think I'm correct in assuming I do a "Find what accesses this address" check on the new added address that points to my value.
But then there is nothing showing up as accessing the address. I try to "end turn" in the game, when I'm certain the value is meant to change and the game crashes.
Is this simply the games anti-debugging or is it something I'm doing wrong here?
Lastly thank you for your patience, it's very much appreciated.
| Description: |
|
| Filesize: |
50.78 KB |
| Viewed: |
9910 Time(s) |
|
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25832
Location: The netherlands
|
 Posted: Mon Aug 26, 2013 2:15 pm Post subject: Posted: Mon Aug 26, 2013 2:15 pm Post subject: |
 |
|
You can give it another try. Sometimes you start the debug at a wrong point. (between two breakpoint events)
It also helps to run the game in windowed mode.
And if that doesn't work, you can resort to the pointerscan or code injection
You already know the last offset is 550, so you can set that the pointer must end with 550 to decrease on the number of results and time needed to scan.
Also, is the address correct? Does the address have ANY effect in the game? (A common mistake is that people look for a pointer thinking that will fix the value not having an effect. It won't)
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
atom0s
Moderator
 Reputation: 205 Reputation: 205
Joined: 25 Jan 2006
Posts: 8587
Location: 127.0.0.1
|
 Posted: Mon Aug 26, 2013 3:42 pm Post subject: Posted: Mon Aug 26, 2013 3:42 pm Post subject: |
 |
|
When you find the process you want to alter, try calling:
| Code: | process = processes[0];
process.EnterDebugMode(); // Add this.. |
To enter debug mode and have the token adjusted as needed.
_________________
- Retired. |
|
| Back to top |
|
 |
Mitch25
How do I cheat?
![]() Reputation: 0 Reputation: 0
Joined: 25 Aug 2013
Posts: 7
|
 Posted: Mon Aug 26, 2013 7:17 pm Post subject: Posted: Mon Aug 26, 2013 7:17 pm Post subject: |
 |
|
I tried pointer scanning but I could only get it down from 30,000,000 results to about 6,000,000. And I need to get another 5 variables to make this whole thing worthwhile so I gave up on that method.
It's annoying that I actually know what I have to do now, but can't do it. I have no idea why things are crashing when trying to "Find out what access/writes to this address" on the address, I guess its just one of those things.
Thanks for the help anyway. Much appreciated.
|
|
| Back to top |
|
 |
Dark Byte
Site Admin
 Reputation: 471 Reputation: 471
Joined: 09 May 2003
Posts: 25832
Location: The netherlands
|
 Posted: Tue Aug 27, 2013 3:30 am Post subject: Posted: Tue Aug 27, 2013 3:30 am Post subject: |
 |
|
6000000 working pointers is pretty good. Just pick one that you like. I recommend the one with lowest number of offsets and lowest values.
Some people say you have to keep rescanning till the list is almost empty, they are wrong. There can be millions of possible usable paths. Especially if it's actually a low level pointer)
Just keep rescanning till the count hardly goes down anymore
Do those other 5 addresses have something in common? (E.g. same memory region) if so,you can just adjust the last offset to point them to the correct address
_________________
Do not ask me about online cheats. I don't know any and wont help finding them.
Like my help? Join me on Patreon so i can keep helping |
|
| Back to top |
|
 |
|

 Reputation: 471
Reputation: 471 Reputation: 471
Reputation: 471 Reputation: 471
Reputation: 471 Reputation: 471
Reputation: 471 Reputation: 205
Reputation: 205 Reputation: 471
Reputation: 471




